Get started with Ubuntu Pro
Overview
New to Ubuntu Pro? This how-to guide will help you understand how to activate your Ubuntu Pro subscription and choose which services to enable. Together, we will identify security updates that are uniquely available with an Ubuntu Pro subscription, and we will apply fixes.
We will start by getting a free, personal subscription. Then we will attach this subscription to your existing Ubuntu LTS machine.
Want to learn more about the benefits of Ubuntu Pro before moving on?
What you’ll learn
- What Ubuntu Pro is and how to use it
- How to check the source of your installed packages
- How to attach an Ubuntu Pro subscription to your existing Ubuntu LTS machine
- How to check for and apply security updates on your Ubuntu machine, including security updates for Ubuntu Universe packages which are only available with Ubuntu Pro
What you’ll need
- An Ubuntu machine running 16.04 LTS, 18.04 LTS, 20.04 LTS or 22.04 LTS
- Sudo access
- An email address, or an existing Ubuntu One account
- Ubuntu Pro client version 27.13.1 or newer
1
Before we start
-
Make sure that you are up to date:
$ sudo apt update && sudo apt upgrade
-
Ensure that you’re running the latest version of the pro client:
$ pro --version
27.13.1~20.04.1
I can see that I am running version 27.13.1, so no need to update. If you run a previous version of the client, you have two options:
- You could wait for the pro client update, which is now released and phased to get to all Ubuntu machines, or
-
Consider bypassing the update phasing and install the latest client version using the following command:
$ sudo apt install ubuntu-advantage-tools
-
When you get the latest client, run apt update again to make sure all package data is up to date.
$ sudo apt update
2
Identify the source repository of your installed packages
First, let’s find out how many deb packages are installed on your machine and from which source:
$ pro security-status
1919 packages installed:
1870 packages from Ubuntu Main/Restricted repository
10 packages from Ubuntu Universe/Multiverse repository
10 package from a third party
29 packages no longer available for download
To get more information about the packages, run
pro security-status --help
for a list of available options.
This machine is receiving security patching for Ubuntu Main/Restricted
repository until 2025.
This machine is NOT attached to an Ubuntu Pro subscription.
Ubuntu Pro with 'esm-infra' enabled provides security updates for
Main/Restricted packages until 2030.
Ubuntu Pro with 'esm-apps' enabled provides security updates for
Universe/Multiverse packages until 2030 and has 1 pending security update.
Try Ubuntu Pro with a free personal subscription on up to 5 machines.
OK, so there are 1919 deb packages installed on your machine.
- 1870 packages are from Ubuntu Main/ Restricted repository which means that they receive Ubuntu LTS updates until 2025. This is covered without any subscription but can be expanded with Ubuntu Pro for an additional 5 years, until 2030.
- 10 packages are from Ubuntu Universe/ Multiverse repository and they come with no security assurance from Ubuntu LTS, but they are covered by Ubuntu Pro.
- And there is 1 security update for the Universe repository available with an Ubuntu Pro subscription.
Note: if you’re currently not using any packages from the Ubuntu Universe repository, that line will not be displayed.
To see the list of packages covered with esm-apps and to identify which packages have pending CVE fixes, run:
$ pro security-status --esm-apps 1919 packages installed: 10 packages from Ubuntu Universe/Multiverse repository Ubuntu Pro with 'esm-apps' enabled provides security updates for Universe/Multiverse packages until 2030 and has 1 pending security update. Run 'pro help esm-apps' to learn more Package names in bold currently have an available update with 'esm-apps' enabled Packages: ansible python3-argcomplete python3-kerberos python3-libcloud python3-ntlm-auth python3-requests-kerberos python3-requests-ntlm python3-selinux python3-winrm python3-xmltodict For example, run: apt-cache policy ansible to learn more about that package.
From the output we identify the list of all packages installed from the Universe repository, and we know that the CVE updated concerns ansible.
Alternatively, if you know the CVE number you want to check, the pro fix command can tell you if the machine is vulnerable or not. As an example, let’s check for the CVE-2021-3583, run:
$ pro fix CVE-2021-3583 CVE-2021-3583: A flaw was found in Ansible, where a user's controller is vulnerable to template injection. This issue can occur through facts used in the template if the user is trying to put templates in multi-line YAML strings and the facts being handled do not routinely include special template characters. This flaw allows attackers to perform command injection, which discloses sensitive information. The highest threat from this vulnerability is to confidentiality and integrity. https://ubuntu.com/security/CVE-2021-3583 1 affected source package is installed: ansible (1/1) ansible: A fix is available in Ubuntu Pro with `esm-apps` enabled. The update is not installed because this system is not attached to a subscription. Choose: [S]ubscribe at ubuntu.com [A]ttach existing token [C]ancel
To fix that we need an Ubuntu Pro subscription. Let’s get one!
3
Get your free Ubuntu Pro subscription
-
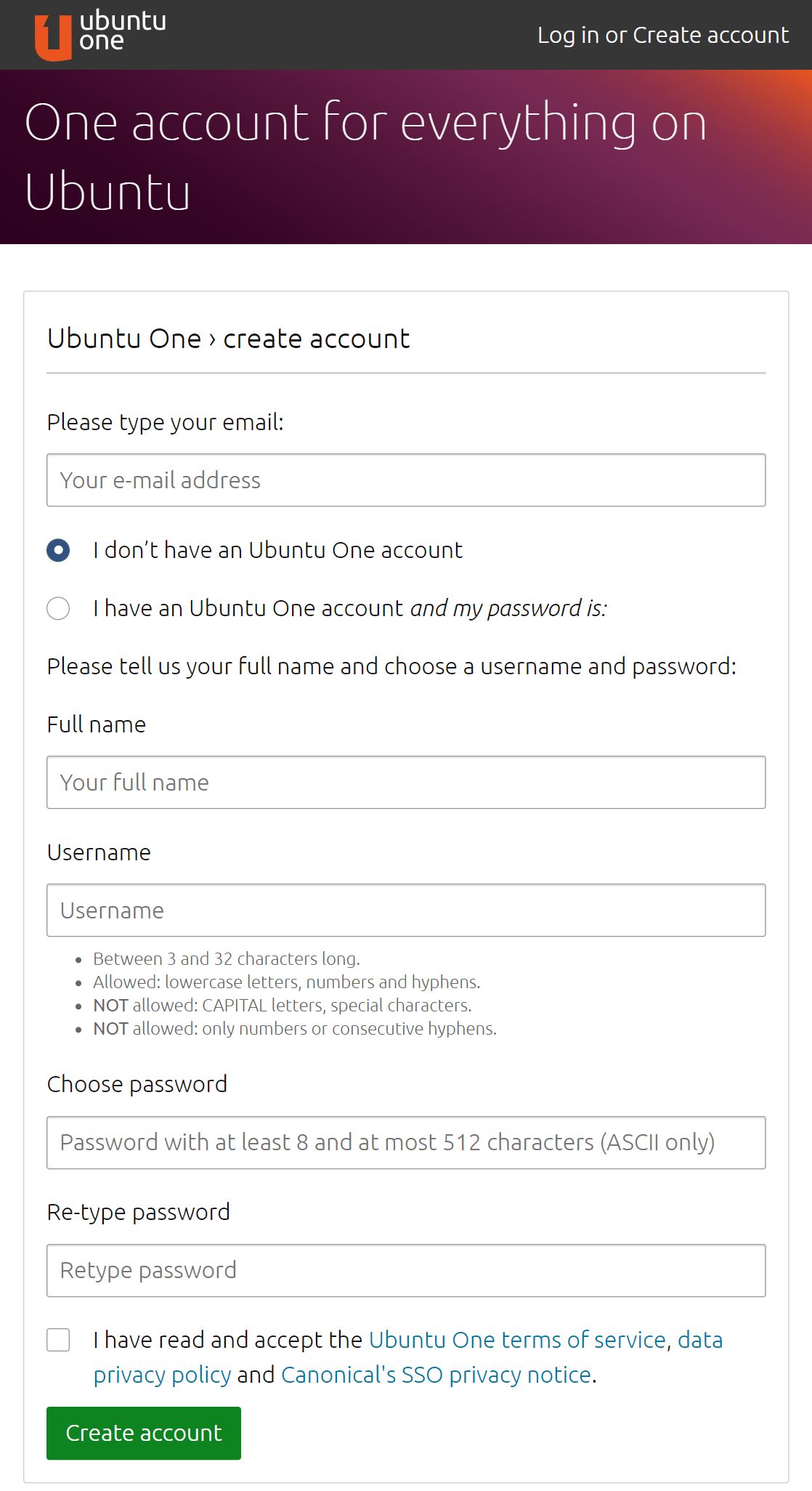
Create an Ubuntu One account
If you do not already have an Ubuntu One account, create one - Ubuntu One is the single account you use to log in to all services and sites related to Ubuntu, including the Ubuntu Pro which is free of charge for personal use on up to 5 machines. For enterprise use-cases go to ubuntu.com/pro/subscribe or contact us.
-
Confirm the email address
Simply click the link provided in the email:
Hello
Welcome to your new Ubuntu One account.
You can log in right away and start using your new account.
Please take a moment to confirm your email address with us.
To confirm your email address, please click on the link below:
https://login.ubuntu.com/Luz1w0n37tidpgi6/token/{YOUR_TOKEN_HERE}/+newemail/{YOUR_EMAIL_HERE}
Thank you,
The Ubuntu One team https://login.ubuntu.com
If you don’t know what this is about, then someone has probably entered your email address by mistake. Sorry about that. Use the following link only if you wish to report this email being incorrectly used:
https://login.ubuntu.com/invalidate-email/{YOUR_TOKEN_HERE}/{YOUR_EMAIL_HERE}
You can also seek further assistance on:
https://help.ubuntu.com/community/SSO/FAQs -
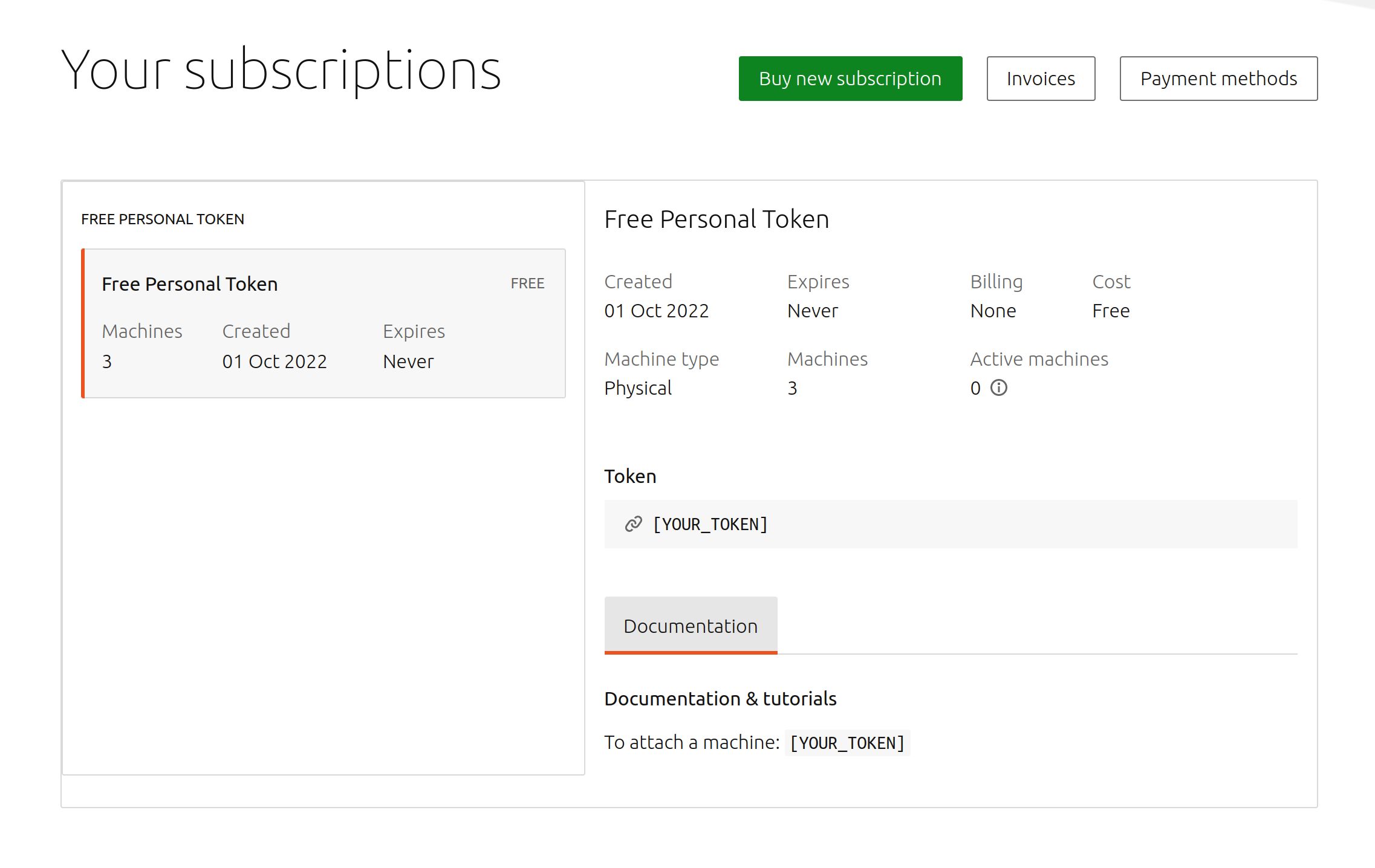
Retrieve the token:
You will be automatically redirected to your Ubuntu Pro dashboard (ubuntu.com/pro/dashboard); an additional Google captcha confirmation step might be required. Your Ubuntu Pro token will be listed under ‘Free Personal Token’
4
Attach your Ubuntu LTS machine to an Ubuntu Pro subscription using the token
Now that we have our Ubuntu Pro token, we can attach it to our Ubuntu instance. Open the terminal on your Ubuntu LTS, and type the following command:
sudo pro attach [YOUR_TOKEN]You should see some of the Ubuntu Pro services automatically enabling, while others will remain disabled until you switch them on:
$ sudo pro attach [YOUR_TOKEN] Enabling default service esm-infra Updating package lists Ubuntu Pro: ESM Infra enabled Enabling default service livepatch Canonical livepatch enabled. Unable to determine current instance-id This machine is now attached to 'Ubuntu Pro - free personal subscription' SERVICE ENTITLED STATUS DESCRIPTION esm-apps yes enabled Expanded Security Maintenance for Applications esm-infra yes enabled Expanded Security Maintenance for Infrastructure fips yes disabled NIST-certified core packages fips-updates yes disabled NIST-certified core packages with priority security updates livepatch yes enabled Canonical Livepatch service usg yes disabled Security compliance and audit tools NOTICES Operation in progress: pro attach Enable services with: pro enable <service> Account: [YOUR_EMAIL] Subscription: Ubuntu Pro - free personal subscription
This output will depend on your Ubuntu LTS version; for instance ‘fips’, ‘fips-updates’ and ‘usg’ are not yet available on Ubuntu 22.04 LTS.
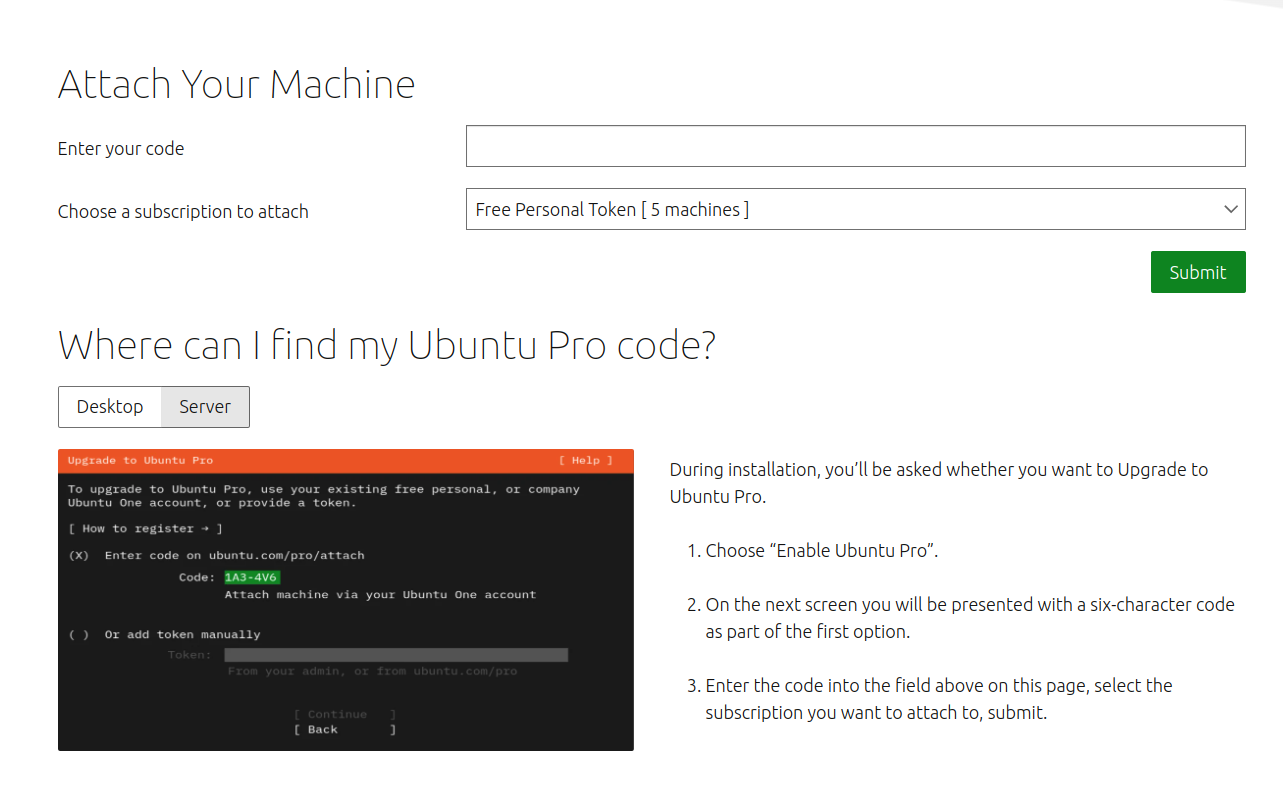
For Ubuntu Desktop, you can go to “Software & Updates” and open the “Ubuntu Pro” tab.
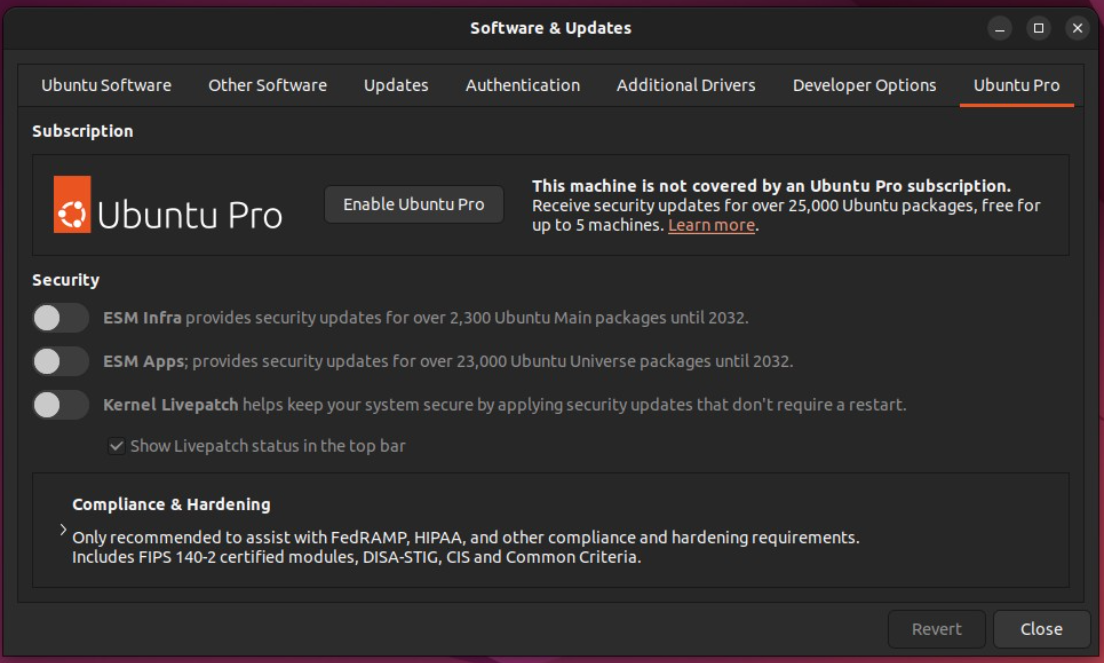
Then you can click the “Enable Ubuntu Pro” button. You can then copy paste the token into “add token manually”.
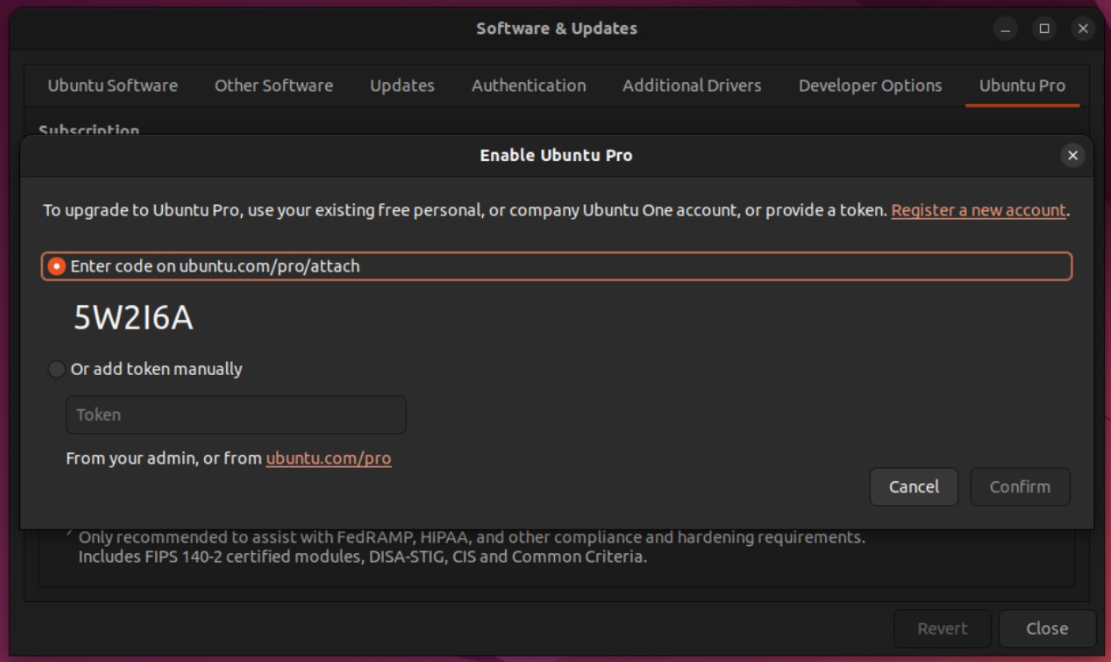
Alternatively, you can pick the code displayed and paste it on ubuntu.com/pro/attach
5
Congratulations - your machine is now upgraded to Ubuntu Pro
Well done! Your machine now has access to Ubuntu Pro repositories. That means that every time you update
your software, you will be pulling from the Ubuntu Pro’s Expanded Security Maintenance repositories. You can get
it through all the usual paths; nothing new to learn. You can use unattended-upgrades, the Software Updater on
the Desktop, or apt upgrade command in the CLI.
To ensure that all available CVE fixes are applied, run:
$ sudo apt update && sudo apt upgrade6
What else can you use your Ubuntu Pro subscription for?
For users running in regulated environments, we have a set of FIPS-certified crypto-modules and hardening scripts available. To enable them, consider enabling other Pro services you are entitled to, such as the Ubuntu Security Guide.
$ sudo pro enable usg7
That’s all, folks
Good job, you made it! You should now know how to access and use Ubuntu Pro, as well as understand all the great benefits Ubuntu Pro has to offer.
Next steps:
Still hungry to learn more about Ubuntu Pro? Talk to the Canonical team or head on over to Ubuntu Pro Discourse.
