Intel® TDX 1.0 technology preview available on Ubuntu 23.10
ijlal-loutfi
on 3 November 2023
Tags: confidential computing , confidential VM , Intel , TDX , Ubuntu
Today’s security landscape faces a significant challenge: the lack of adequate protection for data in active use. Data breaches can happen at runtime (that is, when computation is taking place on a machine’s main memory), stemming from a range of vectors such as malicious insiders with elevated privileges or hackers exploiting vulnerabilities within privileged system software, such as the operating system, hypervisor, or firmware.
Intel® Trust Domain Extensions (Intel TDX) presents a fundamental solution designed to restore control over the security of your workloads. It accomplishes this by enabling them to operate within hardware-protected trusted execution environments. These secure and isolated environments are purpose-built to prevent unauthorised access or alterations to applications and data while they are actively in use, thereby enhancing security for organisations managing sensitive and regulated data.
To harness the strength of these robust security measures, we rely on Intel’s innovations at the silicon level, building on the foundation laid by select SKUs of their 4th Gen Intel Xeon processors and all soon-to-be-launched 5th Gen Intel Xeon processors. However, for end-users to fully leverage these essential silicon security features, the entire software stack that operates atop it must be enlightened.
Within the Linux ecosystem, this requires upstreaming of patches before customers can integrate them into their preferred downstream distributions. This is a time-intensive process. Recognising the pressing need to address security vulnerabilities at run-time, Ubuntu has strategically partnered with Intel, and we now offer Ubuntu users a customised build derived from Ubuntu 23.10, encompassing all the essential components required to construct TDX confidential workloads. These Ubuntu builds cater to both the host and guest sides, empowering users to launch a confidential TDX virtual machine seamlessly.
What is Intel® TDX?
Intel® TDX introduces new architectural elements to create secure, isolated virtual machines known as trust domains (TDs). The primary goal of Intel® TDX is to safeguard TDs from various potential software threats, including the virtual-machine manager and other non-TD software on the platform. Intel® TDX also enhances TD defence against specific physical access attacks on platform memory, including offline dynamic random access memory (DRAM) analysis such as cold-boot attacks and active attacks on DRAM interfaces.
To achieve this high level of security, Intel® TDX incorporates new CPU security extensions that provide three essential security features:
- Memory Isolation through Main Memory Encryption: CPUs equipped with confidential computing capabilities include an AES-128 hardware encryption engine within their memory controller. This engine encrypts and decrypts memory pages whenever there is a memory read or write operation. Instead of storing workload code and data in plain text in system memory, they are encrypted using a hardware-managed encryption key. This encryption and decryption process happens seamlessly within the CPU, ensuring strong memory isolation for confidential workloads.
- Additional CPU-Based Hardware Access Control Mechanisms: CPUs with confidential computing capabilities introduce new instructions and data structures that allow auditing of security-sensitive tasks typically carried out by privileged system software. These tasks encompass memory management and access to platform devices. For example, when reading memory pages mapped to confidential workloads, these new instructions also provide information about the last value written into the page. This feature helps prevent data corruption and replay attacks by detecting unauthorised modifications to memory pages.
- Remote Attestation: Enable a relying party, whether it’s the owner of the workload or a user of the services provided by the workload, to confirm that the workload is operating on an Intel® TDX-enabled platform located within a TD before sharing data with it. Remote attestation allows both workload owners and consumers to digitally verify the version of the Trusted Computing Base (TCB) they are relying on to secure their data.
Ubuntu Intel® TDX stack
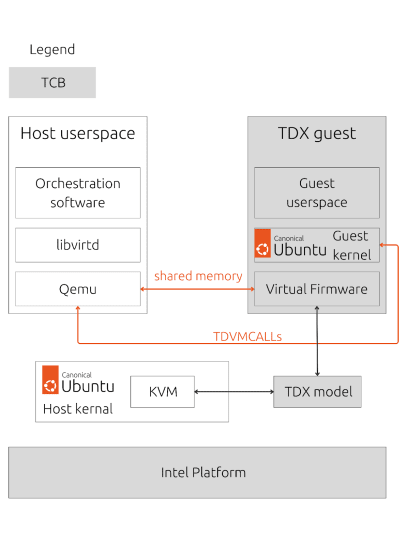
When you have a TDX-capable hardware at your disposal, you are ready to set up the host side by leveraging the customised Ubuntu 23.10 build. This specialised build incorporates a 6.5 kernel, derived from the 23.10 generic kernel. It also includes essential user space components accessible through PPAs, such as Libvirt 9.6, and QEMU 8.0.
On the guest side, the 23.10 build provides a comprehensive package, featuring a 6.5 kernel, Shim, Grub, and TDVF, which serves as an in-guest VM firmware.
Create a TDX Confidential VM with Ubuntu Today
To facilitate building with Ubuntu for Intel® TDX, Canonical offers a set of user-friendly scripts for the customers of its 23.10 TDX custom build. These scripts streamline the process of enabling TDX on both the host and guest sides and simplify the creation of confidential environments with just a few commands. The capability to remotely attest the security of the TDX trusted execution environment is expected to be available in December 2023.
We have made all the set up assets accessible to the public via our GitHub Repository. We encourage everyone to refer to the Readme file within the repository for straightforward instructions on how to get started.
Looking ahead
Our journey with Intel® TDX is an ongoing commitment. Looking ahead to Ubuntu 24.04 LTS, Canonical will remain dedicated to collaborating with Intel, ensuring that we deliver Intel® TDX optimised images that are not only enterprise-ready but also equipped to support production workloads with the highest level of support and security maintenance.
Additionally, with Ubuntu-based Intel® TDX readily accessible on multiple public cloud providers (e.g. Microsoft Azure and Google Cloud), you can confidently embark on building your confidential computing strategy with Ubuntu, spanning across various cloud platforms and within your data centre.
We eagerly anticipate your deployment of the Ubuntu Intel® TDX build and welcome your valuable feedback and questions. Contact us about getting started with confidential computing here. Your input is invaluable as we collectively drive innovation and reinforce data security for the future.
Additional resources
Be sure to check out the following helpful links:
- Contact us
- Join the Intel TDX limited preview today
- Watch our webinar to learn more about confidential computing
- Read our blog post: “What is confidential computing? A high-level explanation for CISOs”
- Read our blog post:“Confidential computing in public clouds: isolation and remote attestation explained”
Talk to us today
Interested in running Ubuntu in your organisation?
Newsletter signup
Related posts
The clock is ticking: Ubuntu Summit 25.10 is just around the corner
London has called, and the Ubuntu community has answered! This year, the Ubuntu Summit has the ambitious goal of extending its reach to everyone, no matter...
Canonical announces it will support and distribute NVIDIA CUDA in Ubuntu
Today Canonical, the publisher of Ubuntu, announced support for the NVIDIA CUDA toolkit and the distribution of CUDA within Ubuntu’s repositories. CUDA is a...
Ubuntu Pro Minimal 22.04 LTS with CIS hardening is now generally available on AWS
August 28, 2025 – We are excited to announce the general availability of Ubuntu Pro Minimal 22.04 LTS with CIS hardening, a new variant of Ubuntu designed for...
