Extreme OpenStack
Canonical
on 3 November 2014
Extreme OpenStack
From instant solutions for big data and platform-as-a-service (PaaS) to a revolution in container technology and the easiest way to build an OpenStack cloud, we will show you exactly why we are the leaders in scale-out technology.
Mark Shuttleworth Keynote
Watch Mark Shuttleworth create high-density container magic, put OpenStack on autopilot, make PaaS and big data instant, and much more.
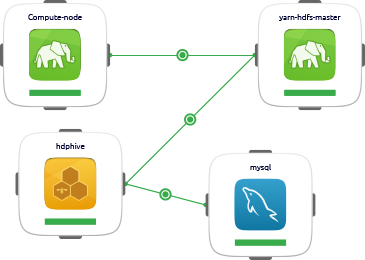
Big data solutions
Structured or unstructured, batch or real-time, build your entire Hadoop workflow with Juju in minutes. Reduce, analyse, index, and visualise your data in four easy steps, re-configure and iterate as often as needed. That is maxim big data from Canonical.
Introducing LXD
Take all the efficiency of docker and turn it into a full virtualisation experience. Launch a new Linux machine in under a second. Launch hundreds of them on a single server. Connect them separately and securely. Run that on one node or a million. On bare metal, public cloud, or OpenStack. This is LXD from Canonical.
Cloud Foundry in minutes
Platform-as-a-Service (PaaS) solutions such as Cloud Foundry are notoriously complex to set up. Canonical’s Juju now lets you deploy and configure an entire CF environment in minutes. You can also use Juju to deploy OpenStack and go from zero to Cloud Foundry on OpenStack in less than an hour!

Now available from Canonical:
-
Extreme Openstack
Maximum performance. Maximum scale. Maximum resilience.
-
Maximum Big Data
The hottest Hadoop, deployed in minutes.
-
Maximum PAAS
Cloud Foundry deployed in minutes.
-
Maximum DevOps
Docker and Juju make cloud magic happen.
-
Maximum Scale
Setting records for fastest and densest deployments at scale.
-
Maximum value
Efficient, flat, AZ pricing for OpenStack.
-
Maximum ecosystem
Thousands of component combinations tested every week.
-
Maximum efficiency
The new hypervisor isn’t a hypervisor, and it’s much, much faster.
-
Maximum ease
The Canonical Distribution lets you build a cloud in your lunch hour.
-
Maximum convenience
Let us build and operate your OpenStack cloud for you.
Talk to us today
Interested in running Ubuntu in your organisation?
