Dustin Kirkland
on 31 October 2016
If you haven’t heard about last week’s Dirty COW vulnerability, I hope all of your Linux systems are automatically patching themselves…
Why? Because every single Linux-based phone, router, modem, tablet, desktop, PC, server, virtual machine, and absolutely everything in between — including all versions of Ubuntu since 2007 — was vulnerable to this face-palming critical security vulnerability.
Any non-root local user of a vulnerable system can easily exploit the vulnerability and become the root user in a matter of a few seconds. Watch…

Coincidentally, just before the vulnerability was published, we released the Canonical Livepatch Service for Ubuntu 16.04 LTS. The thousands of users who enabled canonical-livepatch on their Ubuntu 16.04 LTS systems with those first few hours received and applied the fix to Dirty COW, automatically, in the background, and without rebooting!
If you haven’t already enabled the Canonical Livepatch Service on your Ubuntu 16.04 LTS systems, you should really consider doing so, with 3 easy steps:
- Go to https://ubuntu.com/livepatch and retrieve your livepatch token
Install the canonical-livepatch snap$ sudo snap install canonical-livepatch - Enable the service with your token
$ sudo canonical-livepatch enable [TOKEN]
And you’re done! You can check the status at any time using:
$ canonical-livepatch status --verboseLet’s retry that same vulnerability, on the same system, but this time, having been livepatched…

Aha! Thwarted!
So that’s the Ubuntu 16.04 LTS kernel space… What about userspace? Most of the other recent, branded vulnerabilities (Heartbleed, ShellShock, CRIME, BEAST) have been critical vulnerabilities in userspace packages.
As of Ubuntu 16.04 LTS, the unattended-upgrades package is now part of the default package set, so you should already have it installed on your Ubuntu desktops and servers. If you don’t already have it installed, you can install it with:
$ sudo apt install unattended-upgradesAnd moreover, as of Ubuntu 16.04 LTS, the unattended-upgrades package automatically downloads and installs important security updates once per day, automatically patching critical security vulnerabilities and keeping your Ubuntu systems safe by default. Older versions of Ubuntu (or Ubuntu systems that upgraded to 16.04) might need to enable this behavior using:
$ sudo dpkg-reconfigure unattended-upgrades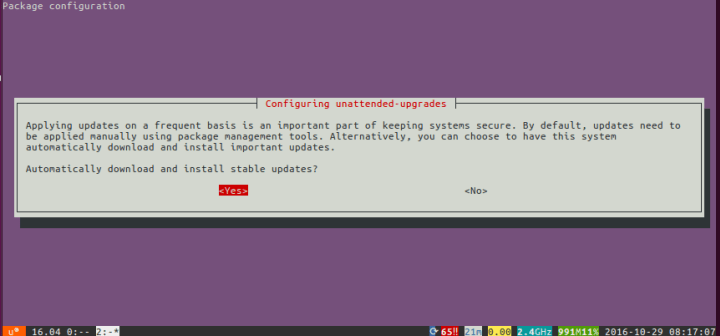
With that combination enabled — (1) automatic livepatches to your kernel, plus (2) automatic application of security package updates — Ubuntu 16.04 LTS is the most secure Linux distribution to date. Period.
If you want to enable the Canonical Livepatch Service on more than three machines, please purchase an Ubuntu Advantage support package from buy.ubuntu.com or get in touch.



