ROS CVE alert; ensuring security for robotics
Gabriel Aguiar Noury
on 5 October 2021
Security for robotics is a priority for ROS developers and crucial for the success of robotics. Open Robotics has registered a CVE that affects ROS Kinetic, Melodic and Noetic. CVE stands for Common Vulnerabilities and Exposures, and it’s an international system that provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. This specific CVE affects ROS users and their security for robotics.
“An infinite loop in Open Robotics ros_comm XMLRPC server in ROS Melodic through 1.4.11 and ROS Noetic through1.15.11 allows remote attackers to cause a Denial of Service in ros_comm via a crafted XMLRPC call.”
Open Robotics has already built and tested the security patch and has made the fix available to the community (e.g. Melodic update). So if you haven’t upgraded your ROS stack, please do so to keep security for robotics.
A Denial of Service attack (DoS attack) is a cyber-attack in which the attacker looks to make unavailable machines or network resources to its final users by interrupting the device’s normal functioning. The infinite loop is what allows attackers to flood the targeted machine or resource with superfluous requests, overloading systems and prevent some or all legitimate requests from being fulfilled. Imagine that you have a group of people crowding the entry door of your shop, making it hard for your legitimate customers to enter, thus disrupting trade.
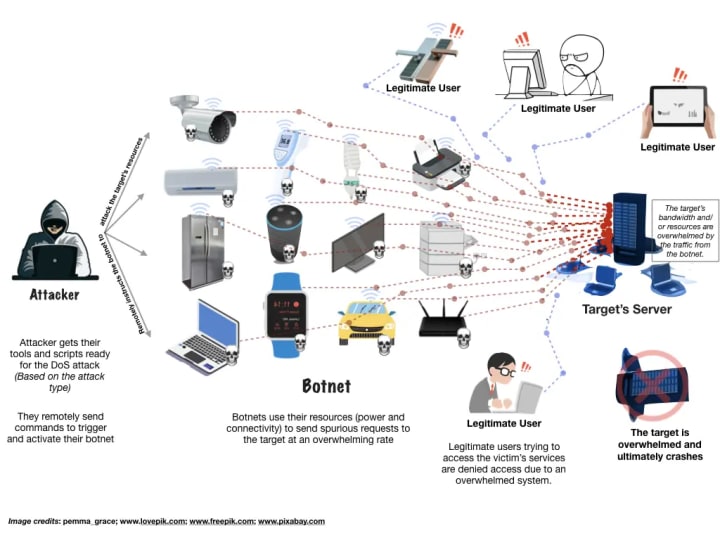
For enterprises that want to reduce operational expenses of security maintenance while leveraging a hardened ROS with 10-year security, make sure to check out ROS ESM. In partnership with Open Robotics, Canonical’s brings its world-class Ubuntu security maintenance infrastructure to ROS. With ROS ESM, the time consuming and resource-intensive work of keeping core ROS packages secure is no longer a problem.
Security for robotics compromised for ROS Kinetic users
If you are still working with ROS Kinetic, the fixes will not be backported to this distribution since it has reached end-of-life. This means that your robots running on Kinetic will be vulnerable to the DoS attack, putting you and your user at risk.
If you have deployed robots using Kinetic we do recommend migrating to supported versions or accessing ROS ESM. With ROS ESM you will continue to get security updates for ROS Kinetic and Melodic for up to 10 years.
- Learn more about Kinetic EOL implications in this video. Or read our ROS support whitepaper.

Setting an example for the community
We want to congratulate Open Robotics for the process undertaken to notify the community about the security threat. The ROS community rarely registers CVEs, impacting its industrial credibility. We need to adopt these habits. A healthy, security-driven community follows standard security practices that help better secure its open-source code. Open Robotics is taking the lead in this community effort and setting an example for others to follow.
Talk to us today
Interested in running Ubuntu in your organisation?
Newsletter signup
Related posts
ROS Noetic is EOL – take action to maintain fleet security
As of May 2025, the Robot Operating System (ROS) Noetic Ninjemys officially reached its end of life (EOL). First released in 2020 as the final ROS (1)...
Discover your fully open source robotics observability at ROSCon 2025
Another year, another ROSCon! This year we’re heading to Singapore, and Canonical is once again thrilled to sponsor this important community event. Just like...
Canonical achieves ISO 27001 certification
The certification demonstrates alignment with cybersecurity standards that will further safeguard open source products and services for use in the most...
