Enable FIPS on Google Cloud
Hugo Huang
on 9 March 2022
Cyber attacks present an imminent threat to our digital assets. And they come in a variety of ways, including computer viruses, Denial-of-service (DoS), hacking, ransomware, memcached. In February 2022, White House deputy national security adviser for cyber and emerging technology Anne Neuberger claimed that the Russian hackers conducted a DDoS attack on the Ukrainian banks and Ministry of Defense before their military attacks. To defend against those threats, people relentlessly develop new Cyber Security technologies, such as AI & Deep Learning that add additional layers of authentication, Behavioral Analytics that helps determine patterns of cyber threats, Embedded Hardware Authentication like Intel’s Sixth-generation vPro Chips, and Zero-Trust Models that assume a network is already compromised. For all cyber security technologies, encryption is considered an essential technology to protect sensitive data. Encryption is a technology that attempts to make the information unreadable by anyone other than the intended recipients. People normally grant their audience access to encrypted data via passwords or decryption keys. On the Internet, encryption technologies include Encryption in transit, such as Virtual Private Network (VPN); and Encryption at rest, such as Encrypted Storage; and Encryption in use, such as Confidential Computing.
FIPS 140-2, the encryption standard for US government
On December 17, 2002, the 107th United States Congress enacted the Federal Information Security Management Act of 2002 (FISMA). FISMA 2002 requires every federal agency to implement an agency-wide information security program for their information systems, including those provided or managed by their contractors and other sources. Pursuant to FISMA law, National Institute of Standards and Technology (NIST) developed the Federal Information Processing Standard (FIPS) Publication 140-2 as a security standard that sets forth requirements for cryptographic modules, including hardware, software, and firmware for U.S. federal agencies. FIPS 140-2 standard provides four levels of security:
- Level 1 – Security Level 1 provides the lowest level of security. Basic security requirements are specified for a cryptographic module, while no specific physical security mechanisms are required beyond the basic requirement for production-grade components. For example, a personal computer encryption board can be a level 1 cryptographic module.
- Level 2 – Security Level 2 improves upon the physical security mechanisms of a Security Level 1 cryptographic module by requiring features that show evidence of protecting against unauthorized physical access.
- Level 3 – Built on top of Level 2, Security Level 3 further prevents the intruder from gaining access to critical security parameters (CSPs) held within the cryptographic module. Security Level 3 also requires physical security mechanisms that have a high probability of detecting and responding to attempts at physical access.
- Level 4 – Security Level 4 provides the highest level of security. Penetration of the cryptographic module is highly likely to be immediately detected, and all plaintext CSPs will be deleted at the same time. Security Level 4 cryptographic modules are useful for operation in physically unprotected environments.
To achieve any of these four Security levels, the cryptographic module needs to pass Cryptographic Module Validation Program, which is a joint effort between NIST and the Canadian Centre for Cyber Security. Obviously, FIPS 140-2 is also a requirement for the Canadian Government and its agencies.
Ubuntu, FIPS certified Operating System
Ubuntu is the world’s most popular operating system in the Cloud, due to its track record of high security and the latest support for thousands of open source packages. Since Ubuntu 16.04 LTS, each long-term support version of Ubuntu has been validated by NIST through Cryptographic Module Validation Program. To date, Ubuntu 16.04 LTS, Ubuntu 18.04 LTS, and Ubuntu 20.04 LTS are all certified under FIPS 140-2. Here I list the FIPS 140 validated components that are available with Ubuntu Pro and Ubuntu Pro FIPS.
| UBUNTU 16.04 LTS | UBUNTU 18.04 LTS | UBUNTU 20.04 LTS | |
|---|---|---|---|
| Linux Kernel (GA) Crypto API | #2962, #3724 | #3647, #4018, #3664 (AWS),#3683 (Azure), #3954 (GCP) | #3928, #4132 (AWS), #4126 (Azure), #4127 (GCP) |
| OpenSSH client | #2907 | #3633 | #3966 |
| OpenSSL | #2888, #3725 | #3622, #3980 | #3966 |
| OpenSSH server | #2906 | #3632 | #3966 |
| libgcrypt | – | #3748 | #3902 |
| StrongSwan | #2978 | #3648 | #4046 |
As NIST is transitioning from FIPS 140-2 to the newer FIPS 140-3 standard, existing certification under FIPS 140-2 will sunset in five years from the validation date. Canonical is preparing Ubuntu for the new certification and intends to provide FIPS 140-3 certified cryptographic packages on a future release of Ubuntu.
Google Cloud, FIPS certified Cloud
FIPS is a standard for cryptographic modules. The cryptographic module that Google Cloud uses is BoringCrypto, which is FIPS 140-2 validated (certificate 3318). So, both data in transit (within Google Global network or outbound to customer end) and data at rest are encrypted under FIPS 140-2 guidelines. And you don’t need to do anything to encrypt the data traffic. Google automatically encrypts data in transition within it global network of data centers. Google uses the Advanced Encryption Standard (AES) with a 128-bit key (AES-128-GCM) to encrypt all VM-to-VM communication between the hosts, and the session keys are rotated periodically. Google Cloud currently uses BoringSSL, the Open Source implementation of TLS protocol, for internal HTTP(S) Load Balancing. Google also builds Envoy proxies for Internal HTTP(S) Load Balancing in FIPS compliant mode. Moreover, all Google Cloud regions and zones support FIPS 140-2 validated encryption. Google’s BoringCrypto module is tested under Ubuntu 18.04 running on POWER( with and without PAA (clang Compiler Version 6.0.1).

Launch your FIPS compliant VM
1. In the Google Cloud Console, go to the VM Instances page:
2. Click CREATE INSTANCE.
3. Set an instance name you like.
4. Select a region and zone you want to run your instance.
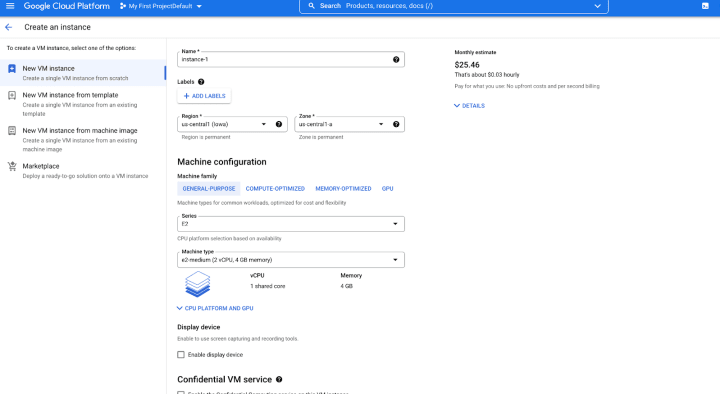
5. Scroll down to the Boot disk options and click Change.
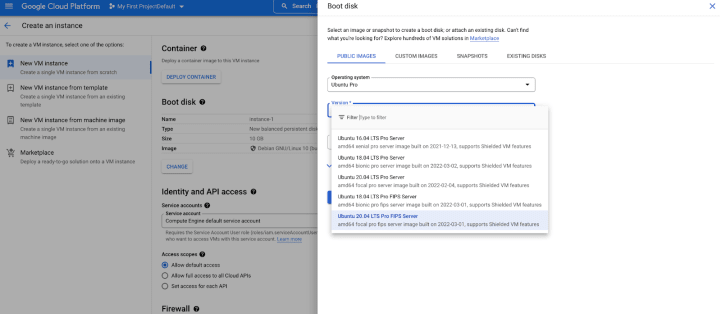
6. In the Boot disk pop-up window, in Operating System, select Ubuntu Pro from the drop-down; in Versions, select FIPS images like “Ubuntu 20.04 LTS Pro FIPS Server”; keep the rest options as default or choose whatever configuration you want; and click SELECT. You now have selected a FIPS-enabled image as your Operating System.
7. Click CREATE to create the instance. Google Cloud also provides the gcloud command-line for you to create the instance in Google Cloud Shell:
gcloud compute instances create ubuntu-fips --zone=us-central1-a --machine-type=e2-medium --image=projects/ubuntu-os-pro-cloud/global/images/ubuntu-pro-fips-2004-focal-v20220301a8. In less than one minute, you will see a FIPS-compliant instance running in your Google Console.
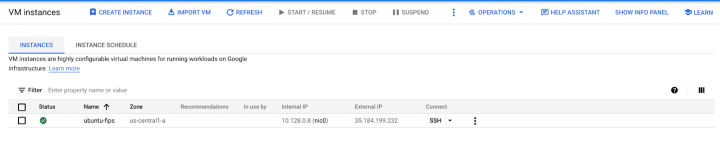
9. Let’s SSH into this instance to verify if it enabled the FIPS module. Click SSH. You will see a pop-up window:
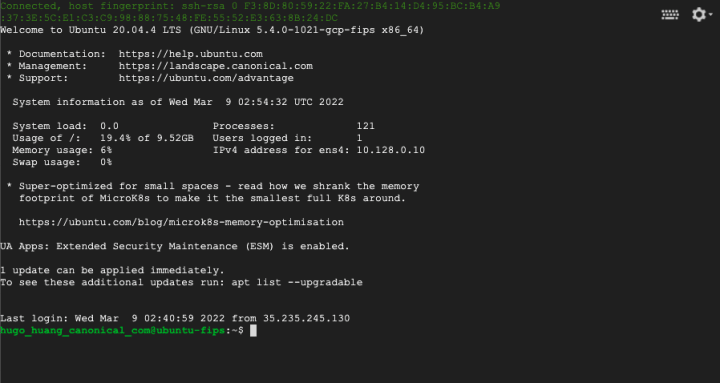
In this window, input:
uname -rWe will see the kernel version of this instance:
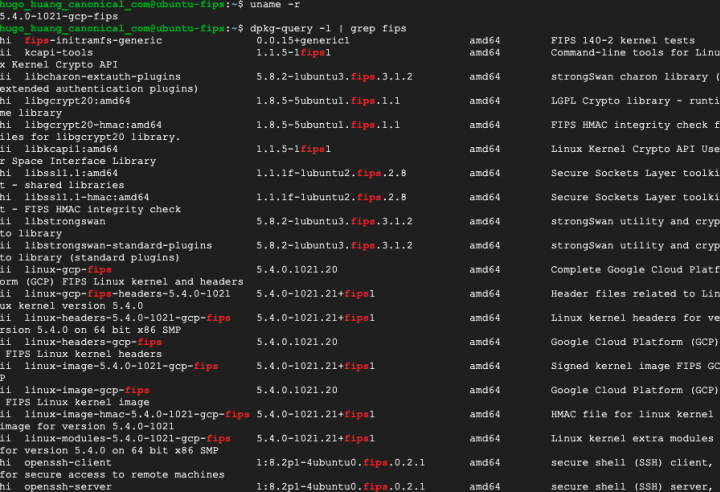
5.4.0-1021-gcp-fipsWe can also check its FIPS packages via this command:
dpkg-query -l | grep fipsYou will find FIPS packages, such as libgcrypt, openssh, libstrongswan, and etc.
Upgrade your VM to be FIPS compliant
From Ubuntu Pro to Ubuntu Pro FIPS
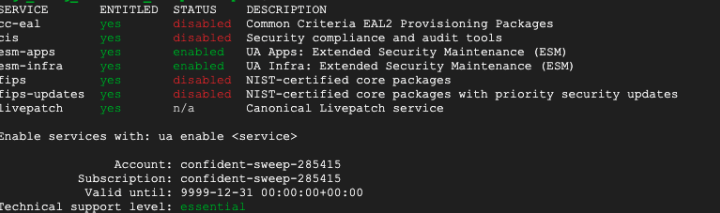
If you are running Ubuntu Pro, in order to enable FIPS kernel, you need to SSH into this machine, input the following:
ua statusYou should see:
Then enable FIPS:
sudo ua enable fipsOne moment, checking your subscription first
This will install the FIPS core packages.
Are you sure? (y/N) y
Updating package lists
Installing FIPS packages
FIPS enabled
A reboot is required to complete install.You can either type “sudo reboot” in the SSH window or reboot the instance in your Google Cloud Console.
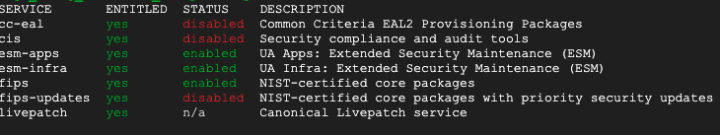
When the machine successfully restarts, you can SSH into it again and input:
ua statusYou should see:
From Ubuntu LTS to Ubuntu Pro FIPS
You may have been running your mission-critical workloads on Ubuntu LTS. You don’t want to migrate them to a FIPS-compliant environment, because we all know that migrations mean a lot of work and are full of uncertainties. The good news is, you don’t have to! Stay with your current virtual machines. Google and Canonical have been working together to give you the most seamless experience while getting a FIPS-compliant production environment. Today, you can upgrade your Ubuntu LTS to Ubuntu FIPS in one minute.
Suppose you have one VM running on Ubuntu 18.04 LTS. Here is how it works:
- Step 1: Stop that machine
gcloud compute instances stop $INSTANCE_NAME- Step 2: Append Ubuntu Pro license to the disk
gcloud beta compute disks update $INSTANCE_NAME --zone=$ZONE --update-user-licenses="https://www.googleapis.com/compute/v1/projects/ubuntu-os-pro-cloud/global/licenses/ubuntu-pro-1804-lts"- Step 3: Start the machine
gcloud compute instances start $INSTANCE_NAMEAnd that is it! Now you have upgraded your Ubuntu 18.04 LTS into Ubuntu 18.04 Pro. Next, please follow the steps in the previous paragraph “From Ubuntu Pro to Ubuntu Pro FIPS”. As a reminder, you simply input this command after you SSH into the running instance:
ua enable fips
sudo rebootPlease note the License URI you inputted in Step 2 is depend on the version of your Ubuntu:
| Ubuntu Pro version | License URI |
| Ubuntu Pro 18.04 LTS | https://www.googleapis.com/compute/v1/projects/ubuntu-os-pro-cloud/global/licenses/ubuntu-pro-1804-lts |
| Ubuntu Pro 20.04 LTS | https://www.googleapis.com/compute/v1/projects/ubuntu-os-pro-cloud/global/licenses/ubuntu-pro-2004-lts |
According to your Ubuntu version, your command should be:
gcloud beta compute disks update BOOT_DISK_NAME \
--zone=ZONE \
--update-user-licenses="LICENSE_URI"Replace the following:
- BOOT_DISK_NAME: the name of the boot disk to append the license to
- ZONE: the zone containing the boot disk to append the license to
- LICENSE_URI: the license URI for the version of Ubuntu Pro you are upgrading to.
For comprehensive instruction, please refer to official Google Cloud documentation: Upgrade from Ubuntu to Ubuntu Pro.
Talk to us today
Interested in running Ubuntu in your organisation?
Newsletter signup
Related posts
Canonical achieves ISO 27001 certification
The certification demonstrates alignment with cybersecurity standards that will further safeguard open source products and services for use in the most...
What our users make with Ubuntu Pro – Episode 2
How Vaultara achieved FedRAMP compliance with Ubuntu Pro Ubuntu Pro helps businesses worldwide to innovate and shape the future. In this edition of What our...
What are dependencies, and how do you secure them?
There are thousands of free-to-use, ready-built programs and code repositories that solve problems you’d otherwise need to spend weeks building the solutions...
